Mastering the Multi-Cloud Connectivity Maze with the Right SD-WAN Partner
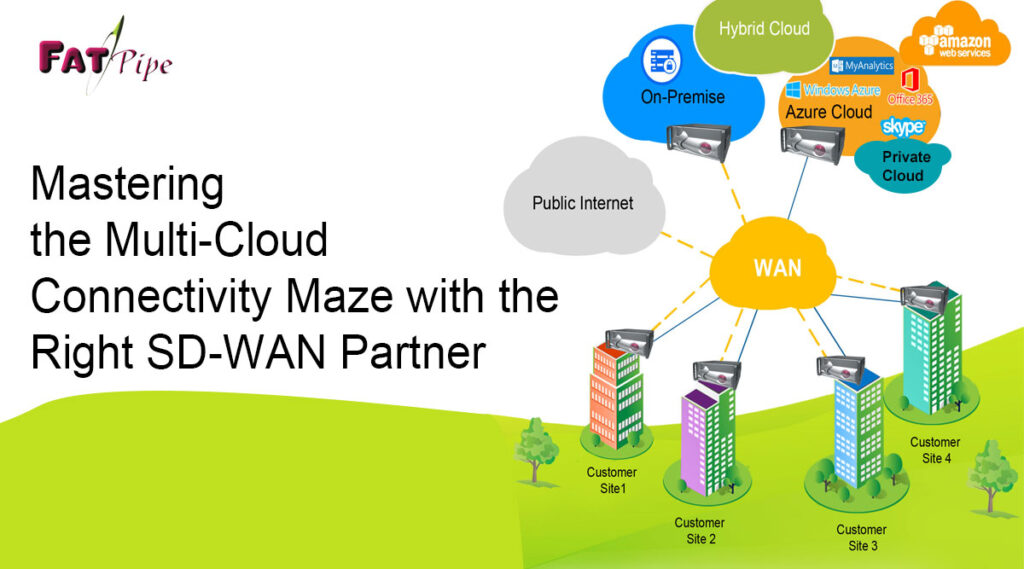 In today’s dynamic business landscape, enterprises are navigating an intricate maze of multi-cloud environments, seeking the perfect synergy between performance, security, and flexibility. As the digital realm evolves, the importance of a robust and strategic SD-WAN solution becomes paramount. SD-WAN simplifies and streamlines the complexities of multi-cloud connectivity, ensuring reliable, secure and efficient network performance across a spectrum of cloud platforms. One major point which cannot be ignored while selection of SD-WAN provider is the seamless integration with SASE offerings preferably from the same SD-WAN provider.
In today’s dynamic business landscape, enterprises are navigating an intricate maze of multi-cloud environments, seeking the perfect synergy between performance, security, and flexibility. As the digital realm evolves, the importance of a robust and strategic SD-WAN solution becomes paramount. SD-WAN simplifies and streamlines the complexities of multi-cloud connectivity, ensuring reliable, secure and efficient network performance across a spectrum of cloud platforms. One major point which cannot be ignored while selection of SD-WAN provider is the seamless integration with SASE offerings preferably from the same SD-WAN provider.
FatPipe SD-WAN for Multi-Cloud Reliable Connectivity
According to a recent annual outage analysis, cloud, Software as a Service, and digital services attributed to 80% of public outages in 2023, increasing from 66% in 2016. Reliability and quality of experience is essential as far as cloud is concerned. Traditional networks often backhaul traffic from remote locations to a centralized data center before accessing cloud services. SD-WAN allows direct access to cloud applications and services, reducing latency and improving the user experience. This direct access enhances reliability by minimizing the dependency on a single centralized point.
FatPipe SD-WAN enables customers who utilize Azure or AWS applications to gain a better experience by overcoming the need to reconnect frequently when the sessions break, which is possible through patented FatPipe SD-WAN technology. This becomes a concern of paramount importance for customers and offices where large groups need to use cloud-hosted applications wherein a single line connection to AWS or Azure is not sufficient to address line drop issues.
FatPipe SD-WAN’s Solutions for Multi-Cloud Connectivity Challenges
Faster TCP Connection Setup Time
FatPipe SD-WAN significantly reduces the TCP connection set-up time by effectively utilizing cross-border cloud communications. This improvement ensured quicker and more efficient establishment of connections. The result is a streamlined and accelerated network experience, mitigating delays and enhancing the efficiency of data transmission across diverse geographic locations within a multi-cloud environment.
Dynamic Load Balancing for Optimal Resource Utilization
FatPipe SD-WAN solution intelligently assesses real-time conditions, directing traffic along the most efficient routes. This dynamic load balancing not only enhances network performance but also contributes to the seamless integration of multiple cloud environments. By ensuring optimal resource allocation, FatPipe SD-WAN solution fosters an agile and responsive multi-cloud connectivity framework, overcoming challenges associated with uneven workloads and diverse cloud architectures.
Enhanced Security with End-to-End Encryption
As data traverses diverse cloud environments, FatPipe SD-WAN employs robust encryption protocols to safeguard information from potential threats and unauthorized access. This end-to-end encryption makes sure that sensitive data remains secure throughout its journey across multiple cloud platforms, addressing the inherent security challenges associated with the diverse architectures of various cloud providers.
Seamless Integration of FatPipe SD-WAN with SASE offerings
FatPipe provides myriad of SASE offerings which seamlessly integrate with our SD-WAN products providing enhanced end user experience. Customers can procure SD-WAN and SASE licenses simultaneously, or time lapse in procurement of SD-WAN and SASE is also possible.
Legacy SD-WAN solutions lack the efficiency to simplify and automate branch-to-cloud connections, hindering the seamless integration needed for an efficient cloud journey. FatPipe SD-WAN emerges as a pivotal solution, addressing the shortcomings of traditional WAN architectures and legacy SD-WAN offerings. It supports innovative approaches including tunnel-less connectivity that involves establishing direct, site-to-site connections without the need for traditional VPN tunnels and without the need for specialized routing protocols. FatPipe SD-WAN’s application-defined focus, autonomous capabilities, and cloud-enabled approach with SASE offerings positions it as a comprehensive solution for organizations seeking a seamless and secure transition to a cloud-centric infrastructure.