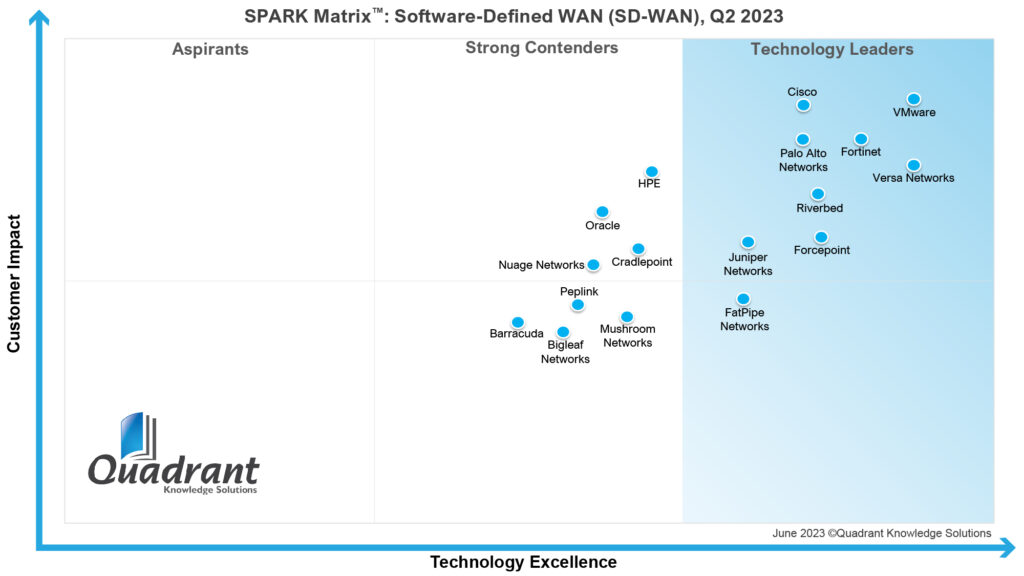
FatPipe Networks Recognized as a Technology Leader in Quadrant’s Spark Matrix
 Quadrant Knowledge Solutions, which is a global advisory and consulting firm, announced that it named FatPipe Networks a 2023 technology leader in the SPARK Matrix Software-Defined Wide Area Network (SD-WAN), Q2 2023.
Quadrant Knowledge Solutions, which is a global advisory and consulting firm, announced that it named FatPipe Networks a 2023 technology leader in the SPARK Matrix Software-Defined Wide Area Network (SD-WAN), Q2 2023.
FatPipe is happy that our commitment to innovation and excellence has been honored. This achievement encourages us to continue excelling and delivering cutting-edge solutions to our valued customers. In the words of Quadrant Knowledge Solutions, “FatPipe Networks offers a robust SD-WAN solution that incorporates FatPipe’s patented Multi-Path security and provides agile deployment and management across the entire fleet of branch offices.. With overall strong performance across the parameters of technology excellence and customer impact, FatPipe Networks has been positioned among the 2023 technology leaders in the global SD-WAN market.”
SD-WAN Market: An Overview
The development of the SD-WAN market highlights its increasing indispensability across diverse business verticals. Positioned beyond a technological trend, SD-WAN has evolved into a strategic necessity for enterprises of all types.
- The SD-WAN market size is forecasted to grow at a CAGR of 29.02% between 2023 and 2028.
- The market size is predicted to increase by USD 13.66 billion.
Key Market Drivers and Insights
The SD-WAN market is driven by several key drivers, including the growing demand for cloud-based applications and services, the need for a centralized network management system, the increasing popularity of SD-WAN as a service, enhanced network visibility and security, and cost-efficiency.
SD-WAN is a must-have solution in a digital landscape where seamless connectivity is pivotal for operational efficiency. Its ongoing progress reflects the growing urgencies of contemporary business landscapes, establishing SD-WAN not as a discretionary option but as an essential enabler for organizations striving to excel in an interconnected and dynamic global environment. SD-WAN is as strong as ever, and it is appreciably addressing data, network automation, efficiency, and security demands by relying on several supporting technologies.
FatPipe Networks has always been at the forefront of technology. Its emphasis on best-of-breed products demonstrates superior performance, specialized functionality, and a competitive edge. The commitment to outstanding customer service has propelled FatPipe to be recognized as a technology leader by Quadrant Knowledge Solutions. It’s not just technological efficiency but a dedication to meeting customer needs that has placed FatPipe in this coveted position.