Part 2: FatPipe SD-WAN for Network Administrators
What Network Administrators Should Look for in a Good SD-WAN: Part 2 of Our SD-WAN Insights Series
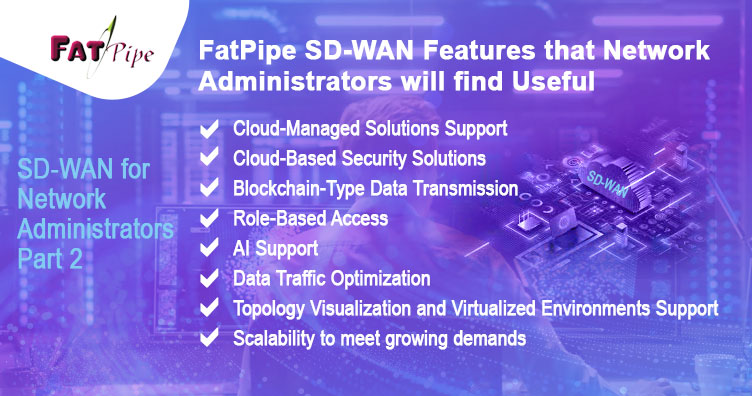
As stated in our previous blog on “What Network Administrators Should Look for in a Good SD-WAN: Part 1 of Our SD-WAN Insights Series”, we have shared the next set of FatPipe SD-WAN features that network administrators will find useful.
Cloud-Managed Solutions Support: FatPipe solutions offer flexible deployment options, including on-site, in the cloud, or as a service, providing network administrators with the freedom to choose the best setup for their organization’s needs and budget.
Cloud-Based Security Solutions: FatPipe unique technical cloud security features aka SASE can help you accelerate the transition to the SASE architecture. The tailored implementations align with your organization’s unique needs with cloud-based firewall, ZTNA, threat protection, Intrusion Detection, and Intrusion Prevention.
Blockchain-Type Data Transmission: FatPipe has invented a unique way of securely transmitting data over lines with multi-path security also known as MPSECTM, which provides an additional level of fortification that obfuscates internet traffic, making it almost impossible to decrypt, through a mechanism similar to blockchain technology.
Role-Based Access: Boosting collaboration through role-based access, making it easier to coordinate across teams. Network administrators can swiftly organize and set access for total groups of users.
AI Support: FatPipe AI for SD-WAN support adds intelligence to network management, automating troubleshooting and optimization.
Data Traffic Optimization: The Edge is enabled with multiple WAN Optimization techniques making it more intelligent. FatPipe data compression technology can compress data by up to 8x. FatPipe’s de-duplication technology looks for data duplicates in data sets and eliminates them. By caching local copies of transmitted data, FatPipe technology reduces the strain on network resources.
Topology Visualization and Virtualized Environments Support: It ensures efficient planning and documentation of network setups.
Scalability to meet growing demands: FatPipe SD-WAN is designed to expand seamlessly, supporting increased bandwidth, additional locations, and more complex application requirements without compromising performance.
FatPipe has been in the forefront of providing innovative solutions through its products including SD-WAN and its flagship product MPVPN. FatPipe MPVPN® is an intelligent and adaptive SD-WAN with additional security with FatPipe’s MPSecTM. Wait for the next blog in this series where we will delineate FatPipe features that can come in handy for CTOs and CIOs.